GoSearch22 is an Off-Shoot of macOS-Targeting Pirrit Adware
Akshaya Asokan (asokan_akshaya) •
February 20, 2021
See also: Live webinar | The EVIL-Ution of Ransomware In 2021-Highest Protection Recommendations
In a blog post, independent macOS security researcher Patrick Wardle notes that the application called GoSearch22 is a malicious adware questioned as a Safari extension. It says the malware is capable of stealing browser data from the victims and acts as a stable agent for further settlement.
Wardle says the malware was first uploaded to VirusTotal in December 2020 and says this is the first variant ever that can run natively on Apple’s M1 chips.
“Apple’s new M1 systems offer a number of benefits, and natively compiled arm64 code runs very quickly,” Wardle says. “We built on the fact that malware authors have now entered the levels of developers… (re) adding their code to arm64 to get native binary compatibility with the product- Apple ‘s latest hardware. “
Malware Variant
Wardle says GoSearch22 is a preview of Pirrit adware, which has been active since 2016. Pirrit is known to target macOS-only devices to steal data from victims and spy on people’s web browsing. Adware is distributed primarily as anti-virus software or as Apple supported apps.
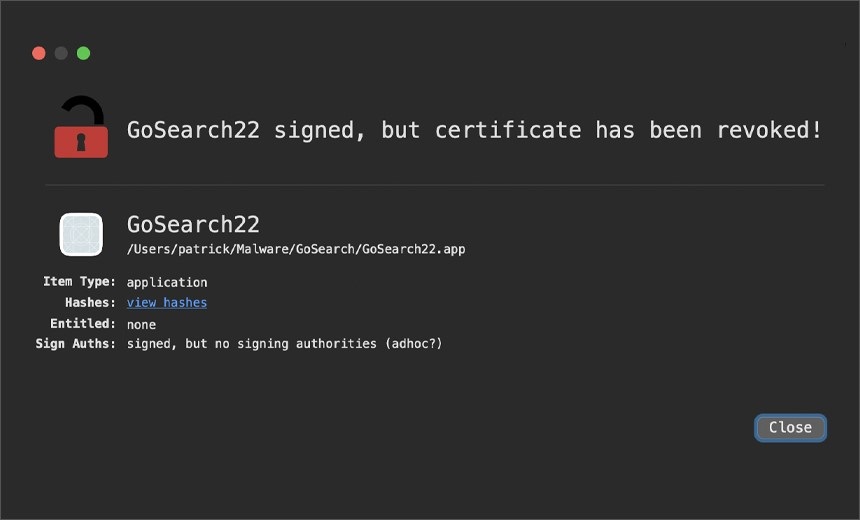
GoSearch22 goes crazy as a Safari extension, signed with an Apple developer ID to avoid detection. The malicious application collects the victim’s browsing data such as IP addresses, addresses of web pages visited, submitted search queries, geolocations and other information related to browsing.
There are two versions of the malware – the arm64 version and the x86_64 version – however, due to the highly obfuscated nature of the malware code, the variables are not easily identifiable, Wardle says.
He says the app’s certificate is maliciously revoked by Apple, noting that it’s not currently available. However, the details of the disease are not clear. Apple did not immediately respond to a request for comment.
James McQuiggan, a security awareness candidate at KnowBe4, says that macOS devices are becoming increasingly targeted, as many users believe that Mac devices are not as vulnerable as Windows. “Cybercriminals are recognizing that the Mac systems are being used more and more by humans, especially now with the M1 systems at a lower cost than the Intel – based hackers. However, the malware was adware, which is largely annoying the user with pop-up ads, browser redirects for searches and it is possible to remove it without resetting the operating system, which is an opportunity for attack Windows malware. “
Pirrit Initiatives
Pyrrit adware has captured thousands of macOS devices since it became active. A 2017 report by Amit Serper, a security researcher at Cybereason, notes that the adware was developed by an Israeli tech company called TargetingEdge.
The researcher found that there were several versions of Pirrit that were able to install fake software or install a proxy server on the victim’s machine to remove the browser. The researcher notes that the later versions use AppleScript ‘s write / autocomplete language to pinpoint the victims and run with basic privileges.
A 2020 report by the security company ESET found that adware is the most common attack vector for hackers targeting Mac devices. The report also noted that 4.9% of threats on Mac devices in the second quarter of 2020 were caused by Pirrit adware.