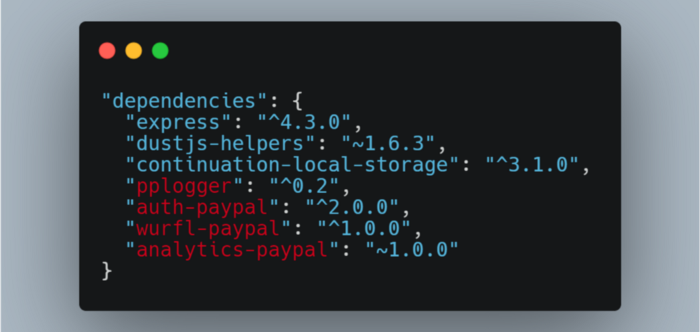
A security researcher has discovered a security vulnerability that allowed it to run code on internal systems owned by major companies, including Apple Inc., Microsoft Corp., Netflix Inc., PayPal Holdings Inc., Tesla Inc. . and others by taking advantage of open source investments.
The supply chain attack was described late Tuesday by ethical researcher and hacker Alex Birsan and involved uploading malware to open source sources including PyPI, npm and RubyGems which was then dispersed downstream.
According to Bleeping Computer, the victims did not need the supply chain attack because they automatically received the malicious code due to a design flaw in open source ecosystems called “through- mutual dependence. ”The device, also known as“ surrogate attack ”by Microsoft Corp., allows threat operators to insert malicious code into private code repositories by simply registering internal library names on indexes. public, open source.
Starting with a malicious node package uploaded to the npm table, Birsan then went further into other sources to see how long it could take advantage of.
“To strike a balance between being able to identify a group based on the data and the need to avoid overly sensitive information, I decided to simply record the username, hostname, and custom path of each specific installation,” Birsan explained. “Along with the external IPs, this was just enough data to help security teams identify potentially vulnerable systems based on my reports.”
Microsoft has also published a white paper on the subject of the dangers of this type of attack. “One common hybrid arrangement that clients use is storing inbound packets on private food but allowing them to recover dependence from public food,” notes Microsoft’s white paper. “This ensures that the latest package notifications are automatically accepted when they are referenced from a package that does not need to be updated. In-house developers publish their packages for this private food and consumers explore both private and public foods for the best available versions of the essential packages. This arrangement poses a supply chain risk: the substitute attack. ”
Craig Young, chief security researcher at cybersecurity and compliance solutions company Tripwire Inc., told SiliconANGLE that this is a real business problem.
“Organizations have a steady stream of options between restarting all wheels, entering costly license contracts or using open source software,” Young explained. “Adopting open source has made many businesses a success while at the same time keeping down the cost of initial development at the expense of supply chains. Software development companies should be tuned in to all the changes that take place within an external software but in reality, this is next to impossible for software projects that are even more complex. ”
The problem he added is that dependency chains can get out of control quickly, and there are often good reasons for requesting quick updates such as security or a common bug fix.
“Identifying, interpreting and analyzing thousands of lines of code could potentially offset open source cost savings for some organizations,” he said. “When software development companies allow their employees to download and start working with non-regulatory coding models from public sources, they are exposing both security and legal risk. In this case, it was a researcher with a ‘home phone’ payment charge, but it could just as easily be the use of a malware implant or patent patent using an algorithm with commercial permit. ”
Image Credit: Alex Birsan
Since you are here …
Show your support for our mission with the one-click subscription to our YouTube channel (below). The more subscribers we have, the more YouTube will recommend relevant content and emerging technology content to you. Thank you very much!
Support our mission: >>>>>> SUBSCRIBE NOW >>>>>> to our YouTube channel.
… We would also like to tell you about our mission and how you can help us achieve it. SiliconANGLE Media Inc.’s business model. based on the intrinsic value of the content, not advertising. Unlike many online publications, we do not have a payroll or run banner advertising, because we want to keep our journalism open, without the impact or need to follow traffic.News, commentary and commentary on SiliconANGLE – along with live, unwritten video from our Silicon Valley studio and global video teams at theCUBE – take a lot of hard work, time and money. Maintaining the high quality requires sponsorship support that is in line with our vision of ad-free journalism content.
If you like the commentary, video interviews and other ad-free content here, please take a moment to view a sample of the video content supported by our sponsors, tweet your support, and keep coming back to SiliconANGLE.