

2021 Text with binary code
getty
2020 has been a dangerous challenge for everyone across the globe. It was the year of the virus, from a biological and digital perspective.
We were fascinated by Covid19, a deadly and upsetting virus that changed our lifestyle. Fortunately, there is great progress being made in medicine, and vaccines are on the way. The unexpected happened in 2020, and it was an urgent wake-up call about the need for better pandemic preparedness.
RESEARCH
Similarly, the digital waste of cyber attacks and breaches, was exacerbated by the need for an ecosystem of instant remote operation to avoid Covid19. Hackers took advantage of the gaps in new remote work environments as the surface of the global cyber attack widened dramatically. Governments, companies, organizations and individuals have paid a heavy price from ransomware breaches and attacks – clearly, we were not prepared enough for the digital virus either. 2021 must be the year for cybersecurity preparation.
With most businesses operating remotely, in 2020 hackers launched attacks against an expanded and fully targeted environment. The doubling has almost doubled since 2019. The increase is tied to an expanded attack surface. This is not surprising as nearly 4.6 billion internet users have been active since July 2020, representing 59% of the world’s population. Internet users in the world 2020 | Statista Online crimes reported to the FBI Internet Crime Complaints Center (IC3) were almost quadrangular as a result of the COVID-19 pandemic.
In 2021, work will continue from the home move and cybersecurity will remain a major challenge. according to Cybersecurity Initiatives, cyber is estimated to cost the world $ 6 trillion annually by 2021. Herjavec Group envisions that business will suffer ransomware attack every 11 seconds by 2021. 107 Informative Data Breakdown Statistics for 2020 | Varonis

Costs of Global Cybercrime Damage
Cybersecurity Initiatives
The methods and capabilities of attack for hackers vary across levels of comfort and according to the actors, some of which are related to organized crime groups or, in particular, national states. Financial benefits are still the main motivation behind most cyber attacks. Phishing has become a very tried and tested way to access company and personal data. It is usually done by hiring a fake website that is designed to be similar to the website itself. The purpose of this attack is to trick the user into entering their username and password into the fake login form, which allows the hacker to identify the person -fulang to steal. Hackers can easily impersonate well-known brand websites, banks, and even people you know.
Another way for hackers to take advantage of ransomware is growing. While ransomware has been around for years, it has become a more common method for hackers as they can operate under the guise of harder-to-find cryptocurrencies. Ransomware can host computers, and even entire networks, as hosts for electronic money payments. Cybersecurity Ventures predicts global ransomware damage will cost $ 20 billion by 2021 – 57X more than in 2015. Cybercrime To Cost The World $ 10.5 Trillion Each Year By 2025 .com)
There are many more types of cyber-threats, and their impact is accelerated by machine learning and artificial intelligence technologies that allow hackers to identify vulnerabilities in networks and devices. for a message.
RESEARCH
The fundamental question for most companies and individuals is what can be done to better protect data in an increasingly connected global digital landscape. Below are some basic actions we can take to make ourselves safer.
10 Measures to Protect Cybersecurity in 2021
1) Learn: It starts with gaining a risk management perspective. Learn about what you need to do from open sources. Gather insights from information resources available in the media. Network with those who have knowledge or experience that mirrors your current cybersecurity needs.
2) Create a Cybersecurity Framework: Investigate Cybersecurity Frameworks such as NIST or MITER ATT & CK®. which offers guidance on technical organization and response programs that identify and recommend ways to mitigate gaps for cyber threats. Cybersecurity frameworks are based on lessons learned and are constantly updated to address new threats, including incident response to a breach. Your goal should be to use these frameworks to create barriers to bankruptcy and policies for flexibility.
RESEARCH
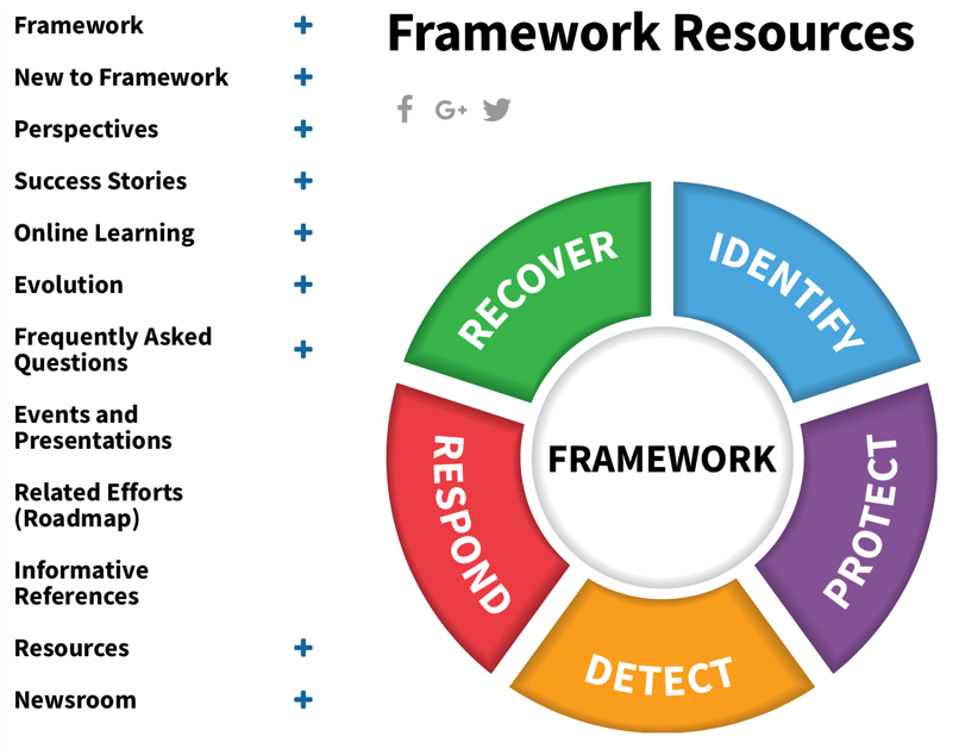
Frame resources
NIST
• www.nist.gov/cyberframework
3) Implement basic cyber hygiene: For example, do you have strong passwords and multi-factor authentication? Do your key data have a backup? Are you using secure WIFI? Do you need to use a virtual private network or encryption? Make sure you update your anti-virus software applications and regularly fix security vulnerabilities as they are updated. Mentioning
back to topic # 1, there are many good lists available on proper cyber hygiene that you can modify as your own. I recommend this CyberAvengers Graphic:

Good cyber hygiene checklist
CyberAvengers
RESEARCH
4) Watch out for social engineering attacks: With so much social media information out there on your likes and dislikes, hackers can find ways to reach out to you with malware through phishing. Always check where the emails or texts are from (not who they want to be from), and do not open any suspicious files. Always be suspicious and work on a zero trust basis when it comes to social engineering threats.
5) The Internet of Things (IoT) has arrived and is preparing for: Each IoT device represents an attack surface that can be a gateway into your data for hackers. A Comcast report found that the average household is hit by 104 threats per month. The most vulnerable devices include laptops, computers, smartphones and tablets, network cameras and storage devices, and streaming video devices, a new report found. Cybersecurity report: Average household hit with 104 threats per month – TechRepublic It is an important step to take change your default passwords on any IoT devices in your network.
6) Consider external security services: If you have small or medium sized businesses, consider bringing in outside knowledge of cybersecurity or a managed service. They can add to your security post with your in-house IT store and conduct vulnerability assessments and recommend solutions and services that are appropriate according to the requirements of your business.
RESEARCH
These are six basic actions to make cyber life easier in 2021. No one is completely vulnerable to breaches, but we can all take steps to improve cybersecurity. Wishing you a cyber-safer, healthier and happier 2021!

A group of people. Human Resources. Global network. Diversity.
getty
Chuck Brooks, President of Brooks Consulting International, is a globally recognized thought leader and subject matter expert Cybersecurity and Emerging Technologies. He is a two-time President-General and served ten years on The Hill as a U.S. Senator on security issues. GovCon & Executive Mosaic named him as one of the top executives on government cybersecurity. LinkedIn named Chuck one of “Top 5 Favorite People to Follow on LinkedIn. Thompson Reuters has been named “Top 50 Global Influencers at Risk, Compliance,” as a “Leading Cybersecurity Expert to be Taken in 2021” by Cybersecurity Ventures, and by IFSEC as the “# 2 Global Cybersecurity Influencer.” ” He was featured in Onalytica 2020 “Who’s Who in Cybersecurity” – as one of the main influencers for cybersecurity issues. Chuck, who is also the Admitted Faculty for Georgetown University Graduate Cybersecurity Risk Programs and Applied Science, briefed the G-20 Power Conference on cybersecurity operating systems. Chuck holds an MA from the University of Chicago, and a BA from DePauw University.
RESEARCH
LinkedIn’s Chuck Brooks Profile:
Chuck Brooks on Twitter: @ChuckDBrooks